Enhancing Security: Leveraging GitHub Advanced Security in Azure DevOps
Accelerate Delivery with Built-In Security

Modern enterprises demand speed and security. GitHub Advanced Security (GHAS) integrates built-in AppSec tools into Azure DevOps, enabling teams to detect vulnerabilities early without slowing down delivery. In 2025, Microsoft has deepened this integration: GHAS can be enabled as an add-on for Azure DevOps Services, embedding secret scanning, dependency scanning, and CodeQL-based code scanning directly into Azure Repos and Pipelines. This unified approach empowers DevSecOps teams to prioritize innovation and security together. For example, as discussed in our AI-Driven DevOps blog on GitHub Copilot and Azure DevOps, integrating intelligence into the pipeline speeds up delivery; GHAS ensures that rapid development does not compromise security by automating vulnerability checks within the same flow.

Why GitHub Advanced Security in Azure DevOps
- Native DevSecOps workflow: GitHub Actions Security (GHAS) is natively embedded in Azure DevOps, allowing developers to integrate security checks directly into their existing CI/CD pipelines. Security tools follow the “push-button” flow of Azure Pipelines and Repos, reducing context switching and manual steps.
- Shift-left vulnerability detection: With GHAS, teams can scan code as it’s written and committed. Secret scanning (push protection and repository scanning) automatically finds exposed credentials and keys. Code scanning, using GitHub’s CodeQL static analysis engine, detects deep code issues such as SQL injection or authentication bypass. Dependency scanning checks open-source libraries for known vulnerabilities. This early detection prevents security issues from reaching production.
- Enterprise-level visibility: GHAS consolidates alerts in Azure DevOps’ Security overview and Boards. The 2025 updates add richer dashboards – for example, a “Risk” tab with filters by project, tool (secrets, code, dependencies), and time. Administrators receive detailed enablement tracking, allowing them to see which projects have scanning turned on for each tool. Such reporting enables executives to gauge their organization's security posture at a glance.
- Integrated licensing and compliance: GHAS for Azure DevOps is billed via Azure subscriptions ($49 per active committer per month) and is eligible for Enterprise Agreements (EAs) through MACC. This simplifies procurement. By embedding security scanning into standard development pipelines, GHAS also helps meet compliance and audit requirements with less overhead – for example, demonstrating that every commit passes secret and vulnerability checks before merging.
Core Features
- Secret Scanning (Push + Repo): GHAS scans every commit (push protection) and can also back-scan a repository for embedded secrets. It recognizes over 200 token types (API keys, passwords, certificates) and checks against more than 100 service providers by default. Exposed secrets are flagged immediately, preventing accidental leaks.
- Dependency Scanning: This pipeline-based scan analyzes the open-source components (both direct and transitive) used by your code. It integrates as an Azure Pipelines task (AdvancedSecurity-Dependency-Scanning@1) after your build steps, fetching vulnerability advisories and flagging insecure libraries. The 2025 updates even added support for modern package managers, such as pnpm v9, ensuring scanning stays current with developers’ toolchains.
- Code Scanning (CodeQL): GitHub Actions Security (GHAS) utilizes GitHub’s CodeQL engine to inspect application code for vulnerabilities automatically. In Azure Pipelines, you add two tasks around your build: AdvancedSecurity-Codeql-Init (configuring languages) and AdvancedSecurity-Codeql-Analyze. CodeQL’s continuously updated query suites look for issues like SQL injection, XSS, auth bypass, etc. By running code scanning in CI, teams catch deep logic flaws early.
- Advanced Visibility and Controls: As of 2025, Azure DevOps offers richer GHAS dashboards. The Security Overview page allows users to filter alerts by project, scan tool, period, and status (new, fixed, or dismissed). Administrators can audit which repos have enabled each scan. Multi-repository publishing is now supported: if your pipeline in Repo A scans code in Repo B, GHAS can infer or explicitly publish alerts to the code’s repo. Preview features, such as service hooks for GHAS alerts (triggering pipelines or tickets on new alerts), are also available to integrate security workflows.
Business Impact
- Reduced Risk of Breaches: By identifying vulnerabilities early (during development or continuous integration), GHAS helps prevent costly security incidents. For example, secret scanning can prevent leaked credentials from circulating, and dependency scanning detects zero-day vulnerabilities in libraries. Studies show shifting left can cut remediation costs by 30–50% (CodeQL identifies issues as code is written, not after deployment).
- Compliance and Audit Readiness: Built-in scanning provides audit evidence that the code was vetted. Enterprises can enforce policies (e.g., fail builds if critical vulnerabilities are detected). GHAS supports compliance frameworks by logging findings and fixes. The centralized view in Azure DevOps, with filtering and auditing, streamlines reporting to regulators or security teams.
- Developer Productivity: Security Does Not Have to Slow Down DevOps. GHAS delivers “security as code” – security engineers define scans and policies once, and developers get automated feedback. 2025 enhancements, like built-in YAML functions for GHAS tasks and manual-validation controls, make pipelines more efficient. Teams spend less time on manual security reviews and toolchains maintenance, focusing on innovation instead.
- Cost Efficiency: Rather than purchasing disparate scanning products, enterprises pay for a single, integrated license model. GitHub Advanced Security on Azure DevOps is billed per active committer and integrates seamlessly with existing Azure billing and support. Many active GHAS customers use their Microsoft agreements (e.g., MACC) to simplify management. The consolidated platform also reduces the overhead of managing separate security tools.
- Strategic Alignment: For executives, adopting GHAS in Azure DevOps aligns with the broader Microsoft ecosystem. It complements efforts like AI-assisted development (e.g. Copilot in Visual Studio) and Azure security services, creating a unified CI/CD pipeline. Embedding security at every step safeguards competitive agility: companies can introduce features faster and more securely, thereby gaining market confidence.
Implementation Approach
- Enable GHAS at the Organization Level: An Azure DevOps administrator must activate Advanced Security in Org Settings. For example, go to Organization settings → Repositories → Security and click “Enable all.” This displays a usage estimate and allows you to begin billing to enable GHAS for all existing repositories. You can also toggle an option to enable GHAS on any new repository automatically. (Licensing must be approved; GHAS features won’t work until invoicing is set up in Azure.)
- Turn On Scanning per Repository: Once GHAS is enabled organization-wide, individual repositories automatically receive Secret Scanning (including repository scanning and push protection) by default. A repository owner or admin can go to the repository’s Security Settings to confirm that secret scanning is active. New or legacy code will be scanned immediately, flagging any detected secrets.
Add GHAS Tasks to Pipelines: For Dependency and Code scanning, modify your Azure Pipelines YAML. Add the Advanced Security Dependency Scanning task (AdvancedSecurity-Dependency-Scanning@1) after your build or package-restore steps. This fetches vulnerability data and reports results to the GHAS dashboard. For code scanning, add AdvancedSecurity-Codeql-Init@1 at the start of the job, specifying the languages, followed by your normal build steps, and then AdvancedSecurity-Codeql-Analyze@1. This sequence runs the CodeQL analysis. For example:
Steps:
- task: AdvancedSecurity-Codeql-Init@1
inputs:
languages: 'java'
enableAutomaticCodeQLInstall: true
- script: ./build.sh # your custom build step
- task: AdvancedSecurity-Dependency-Scanning@1
- task: AdvancedSecurity-Codeql-Analyze@1
This pipeline will compile the code, then run dependency and code scans, and publish any alerts to the GitHub Actions Security (GHAS) overview.
- Configure Multi-Repo (If Needed): If your pipeline checks out code from one repo to scan another (common in infrastructure/IaC scenarios), configure the advancedsecurity.publish—repository variables. By default, GHAS may post findings to the pipeline-defining repository, but you can set advancedsecurity.publish.repository to either true or false.infer: true (to infer from the checked-out repo) or explicitly map it in the pipeline variables. Use the examples in the 2025 release notes to ensure alerts appear in the correct project.
- Review and Tune Policies: Use the GHAS Security overview and Risk page in Azure DevOps to review findings. In the early stages, closely monitor alerts without blocking merges. Over time, enforce stricter gate policies (e.g., fail a PR if a critical bug is found). The new filters and columns introduced in 2025 help track trends. You can also subscribe to service hooks (preview) for GHAS alerts to feed alerts into tickets or chat ops for rapid response.
- Train Teams and Iterate: Ensure developers know how to read GHAS alerts in Azure DevOps—Automate triage by assigning ownership to teams. Regularly update CodeQL query suites and dependencies. Since GHAS tasks run every build, anomalies will surface early. Consider adding architecture diagrams or workflow charts to your documentation:
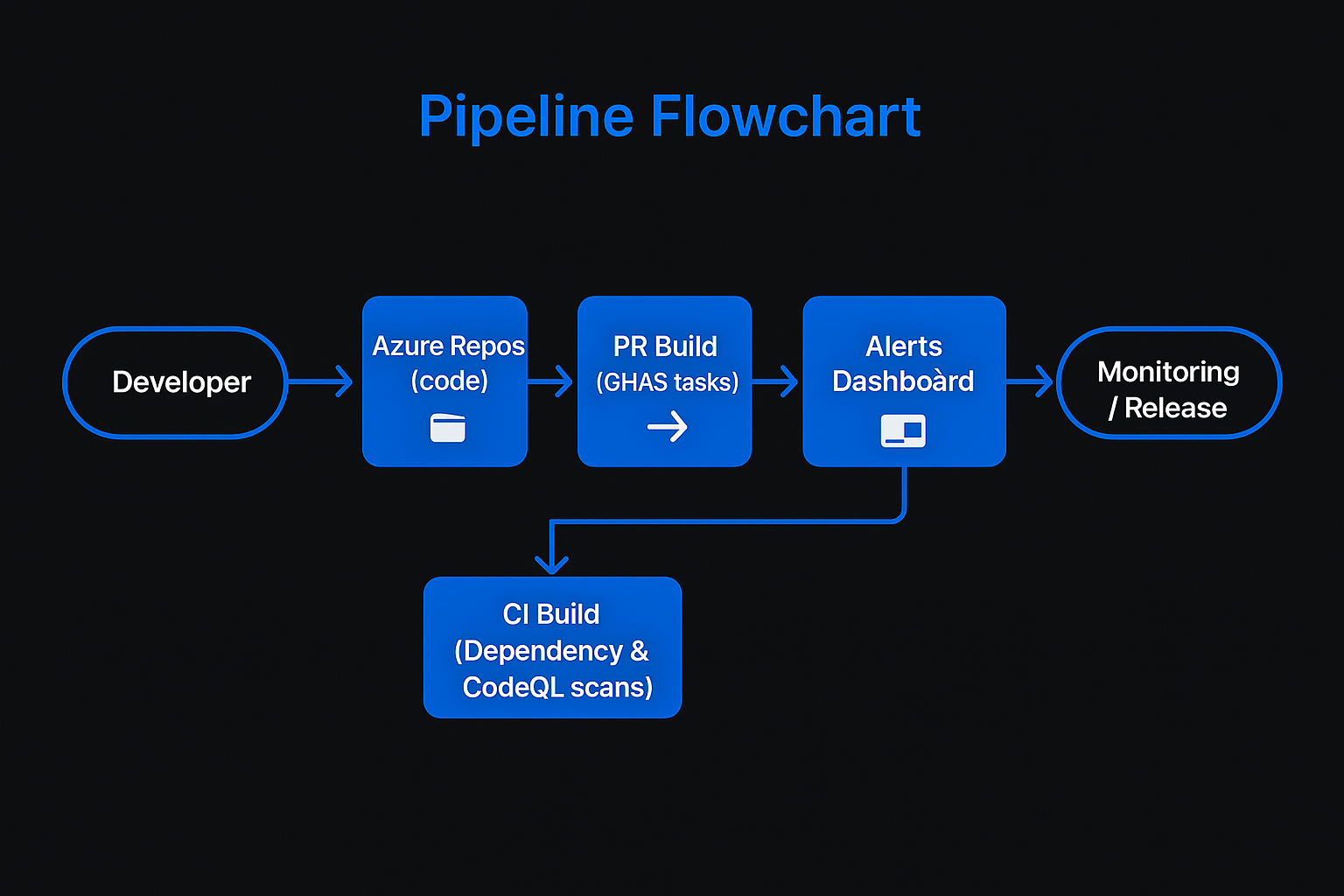
Use Cases
- Early Vulnerability Detection: A new feature branch is built in Azure Pipelines. GHAS CodeQL scanning catches a SQL injection flaw before QA testing. The pipeline breaks immediately, alerting the developer in the GHAS dashboard. Fixing bugs at this stage is far cheaper than after deployment.
- Securing Open-Source Dependencies: A team adds a JavaScript library using npm. GHAS dependency scanning (with support for npm, yarn, pnpm v9, Maven, NuGet, etc.) identifies a known high-severity CVE in that library. The Dev team is automatically warned, and they update the dependency before the build succeeds.
- Preventing Secret Leaks: During migration, an engineer accidentally commits a database password. GHAS secret scanning push protection immediately rejects the push or flags the commit for review. The team removes the secret and rotates credentials before any leak can occur. This avoids the typical post-mortem scramble of certificate rotation.
- Multi-Repo Infrastructure as Code: An IaC pipeline in one repository scans templates in another (e.g., a Bicep or Terraform repo). With the new multi-repo support, GHAS correctly posts infrastructure scan alerts back to the code repository. The result: security fixes are tracked alongside the code that requires changes.
- Executive Dashboards: Security leaders utilize the GHAS Risk dashboard (with filters) to report metrics, such as: “We have X new high/severe vulnerabilities across Y projects this month.” This data-driven view (filterable by tool and date) helps prioritize remediation resources and demonstrates ROI on the GHAS investment.
- Integrating AI and Security: As teams adopt GitHub Copilot to accelerate coding (as discussed in our AI-Powered DevOps blog), GHAS provides the necessary security guardrails. For example, if Copilot suggests code that introduces a vulnerability, the static analysis task will catch it, ensuring that AI-driven productivity does not compromise security.
Conclusion
GitHub Advanced Security closes the gap between rapid development and robust security in Azure DevOps. By embedding secret scanning, dependency checks, and CodeQL analysis right into Azure Repos and Pipelines, GHAS allows enterprises to accelerate delivery with confidence. The 2025 updates enhance this story: improved dashboards, multi-repo support, and pipeline innovations make GHAS easier to enable at scale. For decision-makers, GHAS represents an efficient and centralized way to reduce risk (fewer breaches, improved compliance) and enhance developer efficiency (automated checks within the CI/CD flow).

FAQ'S
1. What is GitHub Advanced Security in Azure DevOps?
GitHub Advanced Security (GHAS) in Azure DevOps brings powerful security tools like code scanning, secret scanning, and dependency review to your Azure DevOps repositories, helping detect vulnerabilities early and enforce secure coding practices during development.
2. How does secret scanning work in Azure DevOps?
Secret scanning automatically detects hardcoded credentials, API keys, and tokens in your Azure Repos. When detected, it alerts developers before code is merged, reducing the risk of exposing sensitive information in production environments.
3. Can I use code scanning on all languages in Azure DevOps?
Code scanning with GitHub Advanced Security supports popular languages like JavaScript, Python, Java, C#, and more. It uses CodeQL to identify security vulnerabilities and code quality issues directly within pull requests and pipelines.
4. How is GitHub Advanced Security integrated into Azure Pipelines?
GHAS integrates with Azure Pipelines via extensions and GitHub Actions for security checks. You can automate scanning during builds and prevent deployments with known vulnerabilities by configuring security gates in your CI/CD workflows.
5. Is GitHub Advanced Security free in Azure DevOps?
GitHub Advanced Security is a paid feature. Microsoft currently offers it as a preview in Azure DevOps, with pricing details expected upon general availability. Organizations can trial features and assess value during the preview phase.

