Azure Arc Architecture: Components and Core Capabilities

In today’s complex cloud landscape, organizations run workloads not only in public clouds like Azure but also across on-premises datacenters, private clouds, and edge locations. Azure Arc is Microsoft’s answer to unifying management, governance, and security across all those environments. This blog dives into its architecture, major components, and core capabilities helping you understand how Azure Arc works under the hood, what problems it solves, and how you can leverage it effectively.
What is Azure Arc?
At its core, Azure Arc enables you to extend Azure’s control plane to resources outside Azure. Resources might be:
- Windows or Linux servers (physical or virtual) in on-premises data centers or other clouds
- Kubernetes clusters in any location
- Data services run on Kubernetes
- Virtualization platforms such as VMware vSphere, SCVMM (System Center Virtual Machine Manager), or Azure Local infrastructure
By “projecting” these non-Azure resources into Azure, you can manage them through familiar tools: Azure Resource Manager (ARM), Azure Policy, Azure Monitor, RBAC (role-based access control), etc.
Why Azure Arc: The Need
Here are key challenges organizations face which Azure Arc addresses:
- Fragmented operations: Different tools, consoles, policies when managing on-prem servers vs cloud resources.
- Governance & compliance: Need consistent policy, security, audit across all environments.
- Data residency or sovereignty: Workloads may need to remain in certain locations but still comply with cloud-native operational practices.
- Edge / disconnected scenarios: Remote edge locations with unreliable connectivity require tools that can manage partially offline operations.
- Hybrid / multi-cloud strategy: Many organizations adopt more than one cloud provider; having unified management reduces complexity and risk.
Azure Arc brings consistent management, unified operations, and security across these domains.

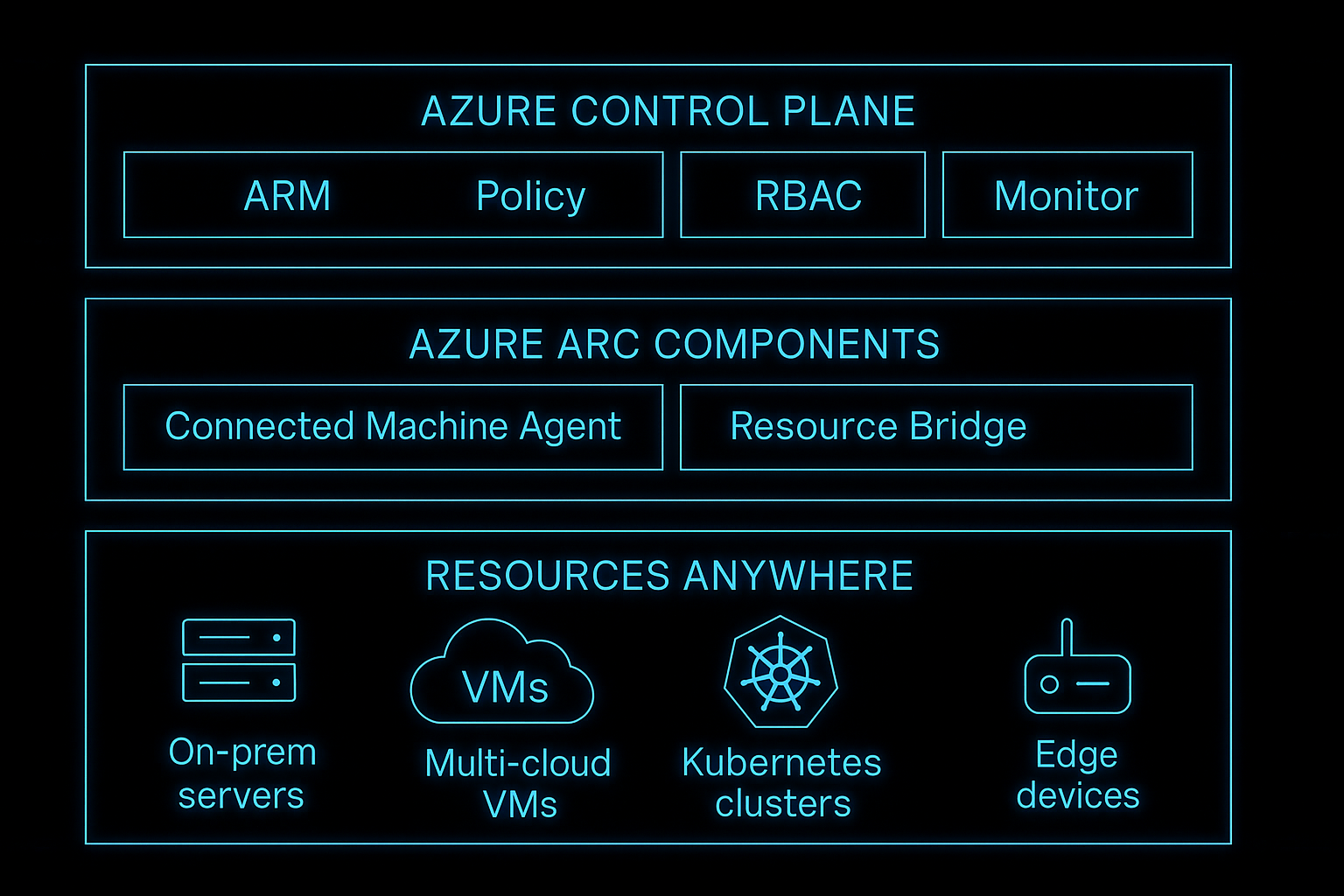
Key Architectural Components
To understand Azure Arc, it's essential to unpack its main components and how they interact. Below are the major pillars:
| Component | What it is / Role | Key Functionality |
|---|---|---|
| Azure Resource Manager (ARM) | ARM is the management plane in Azure where all resources are provisioned, organized, and managed via resource groups, subscriptions, etc. Azure Arc projects external resources into ARM. | Enables you to treat on-prem servers, Kubernetes clusters, databases, etc., as Azure resources. ARM is the hub for tagging, policies, RBAC. |
| Connected Machine Agent | A lightweight agent installed on servers (Windows/Linux) that connects them to Azure Arc. | Facilitates registration, heartbeat, metadata, enabling management, monitoring, policy enforcement for those servers. |
| Arc Agents / Extensions | Components or plugins that enable specific capabilities (monitoring, security, policy enforcement) on Arc-enabled resources. | Examples include Azure Monitor agent, VM extensions, security agents (like from Defender for Cloud), update/patch management. |
| Azure Arc-enabled Data Services / Data Controller | Enables running Azure data services (such as SQL Managed Instance, PostgreSQL Hyperscale) in Kubernetes clusters, either on-prem or in other clouds. The “data controller” is a Kubernetes component that manages these services. | Ensures you can deploy, scale, update, secure database services with cloud style operations while physically located outside Azure. |
| Azure Arc-enabled Kubernetes | Connects Kubernetes clusters regardless of where they are hosted. Adds infrastructure to manage configuration, policy, and deploy apps via GitOps. | Provides unified inventory, governance (with Azure Policy), configuration (via GitOps), monitoring, and control over Kubernetes clusters. Learn more |
| Azure Arc Resource Bridge | A newer component for private clouds & “Azure Local”, enabling projection of on-prem resources into Azure as native resources. Acts as a link or conduit to connect private cloud infrastructure. | Supports self-service provisioning, lifecycle operations (create, delete, start/stop VMs etc), mapping private cloud resource pools to Azure custom locations. Provides foundational control for VMware, Azure Local, SCVMM environments. Learn more |
| Custom Locations | Logical mapping between remote infrastructure (edge, private cloud) and Azure to specify where resources should be deployed. | When deploying resources from Azure to non-Azure infrastructure (via resource bridge), custom locations define the target location. |
| Azure Policy, RBAC, Tags, Resource Graph | Governance & management tools already in Azure but extended to Arc-enabled resources. | Enforcing compliance, role-based access, labeling/tagging for organization, querying inventory across environments, automation. Learn more |
Core Capabilities
Now that we know the components, let’s dive into what Azure Arc enables you to do. These capabilities are what make Azure Arc powerful in hybrid & multi-cloud environments.
- Unified Management & Inventory Once resources are Arc-enabled, they appear in Azure portals, resource groups, etc., just like native Azure resources. This includes physical & virtual machines, Kubernetes clusters, and data services. Collecting metadata, resource status, etc., becomes consistent.
- Governance, Compliance & Policy Enforcement With Azure Policy, you can define rules (e.g., configuration drift, allowed OS versions, encryption settings, tagging enforcement) and enforce them across all Arc-enabled resources. Also, you get visibility into which resources are noncompliant.
- Role-Based Access Control (RBAC) / Security Standard Azure RBAC roles apply to Arc-enabled resources. So permissions, least privilege access, audit of actions are consistent whether the resource lives in Azure or on-premises. Add on tools like Microsoft Defender for Cloud, threat monitoring, etc., across all environments.
- Monitoring, Logging & Insights Using Azure Monitor, Log Analytics, you can collect telemetry from Arc resources. You get performance, health metrics, logs, events. Alerting, dashboarding, analytics all works uniformly.
- Patch, Update & Configuration Management Arc-enabled servers support Update Manager, change tracking, desired state configuration, VM extensions. This reduces drift and ensures servers across cloud/on-premises stay secure and compliant.
- Deployment Flexibility for Data Services Run data services anywhere using Kubernetes. For example, deploying SQL Managed Instance or PostgreSQL Hyperscale on a Kubernetes cluster wherever you want. You get cloud-like experience, compatibility, updates, scaling etc.
- Lifecycle Management for VMs and Kubernetes Clusters Operations like start, stop, resize, delete; upgrades; scaling; cluster operations; configuration. Also self-service VM operations via Azure for on-prem infrastructure (if using resource bridge, Arc-enabled VMware etc.).
- Edge & Disconnected Scenarios, Data Residency Since workloads may be located in remote or edge sites with intermittent connectivity, Azure Arc supports operations that can work with delayed communication, offline modes, or components that sync back when connected. Also allows you to host data where regulations require it while still managing it under Azure frameworks.
How the Pieces Fit Together: An Architectural Flow
To help visualize, here is a typical flow of how Azure Arc components interact to deliver value:
- Onboarding / Registration
- Install the Connected Machine Agent on servers, or connect Kubernetes clusters via the Arc Kubernetes agent. For private clouds or environments like VMware or SCVMM, deploy the Azure Arc Resource Bridge appliance.
- Register resources with Azure; resources acquire Azure resource IDs, appear in Resource Groups, under subscriptions.
- Projection into Azure Control Plane
- Via resource bridge, the non-Azure infrastructure is projected into Azure as Arc-enabled resources.
- Custom Locations map the external environment as target locations for deployment and management.
- Governance & Policy Application
- Define Azure Policies, tags, RBAC etc.
- Apply monitoring, security tools (Defender, etc.), update & patching tools.
- Operationalizing Data Services / Kubernetes / VM Management
- For Kubernetes: use GitOps workflows, deploy and manage containers, lifecycle operations.
- For data services: deploy SQL or other databases on Kubernetes, ensure updates, scale, high-availability.
- For servers: update OS, manage configuration drift, monitor, backup, etc.
- Day-to-day Monitoring, Reporting & Compliance
- Use Azure Monitor, Log Analytics, Alerts, dashboards.
- Use Defender for Cloud, Security Center, auditing logs.
- Automate compliance reporting, drift detection.
- Scaling & Expansion
- As more environments (edge, remote, other clouds) are added, more agents or resource bridges are onboarded.
- Ensuring region, connectivity, and latency planning.
Design Considerations & Best Practices
When architecting a solution with Azure Arc, keep these in mind:
- Connectivity & Network Requirements: Agents and bridges need outbound connectivity to Azure services. Plan for firewall rules, proxy, latency, bandwidth.
- Security & Identity: Use managed identities where possible; ensure certificates, credentials are rotated; ensure resource bridge appliances are secured.
- Region & Data Residency Constraints: Choose Azure regions in which Azure Arc functionality (and specific services you need) are available. Data storage for logs / telemetry should obey residency rules.
- Scalability: Use automation (templates, IaC, GitOps) to standardize onboarding and configuration. Use tagging and management groups to partition workload.
- Offline / Edge Scenarios: For edge sites with unreliable connectivity, ensure agents / bridges can buffer or queue telemetry/configurations, sync when possible.
- Monitoring & Observability: Implement baselines, alerts, dashboards; collect relevant logs, metrics; set up capacity and performance monitoring.
- Cost Management: While some Arc control plane functions are free, many of the services you apply (Monitor, Defender etc.) come with cost. Understand pricing of data services, VMs, monitoring, log storage.
Use Cases
To ground architecture in real world, here are use cases illustrating how components & capabilities are used:
- Retail Chain with Edge Stores A retail company has hundreds of stores, each with local servers & POS systems. They use Azure Arc to onboard each server, apply consistent security, deploy updates, monitor hardware and applications from central Azure Portal, ensuring compliance and reducing manual work in each store.
- Multi-Cloud Database Service Deployment An organization runs Kubernetes clusters in AWS and on-prem. They deploy Azure Arc-enabled data services in those clusters, run SQL at the edge or on-prem, but use Azure’s backup, patching, and monitoring tools, enforcing consistent policies across cloud providers.
- VMware Virtualization Farm A company with extensive VMware vSphere infrastructure wants to use Azure governance tools. They deploy Azure Arc Resource Bridge so they can manage their VMware VMs from Azure, apply policies, RBAC, tag resources, carry out lifecycle operations (start/stop, resize), and view everything from a single dashboard.
Limitations & What to Watch Out For
While Azure Arc solves many problems, it has trade-offs and limitations:
- Dependency on connectivity: Many features require constant or periodic connectivity to Azure; if the agent or bridge is offline, management capabilities may be diminished.
- Latency & performance: Telemetry, policy enforcement etc. across distances may suffer delays; edge scenarios may have performance constraints.
- Versioning & support: Agents, bridges, Kubernetes distributions need to be supported versions; keeping components up to date introduces overhead.
- Feature availability per region: Not all Azure Arc features are available in all Azure regions or for all infrastructure types.
- Cost complexity: Monitoring, log data storage, the data services upstream have costs; optimizing log volume, retention, etc. is essential.
Looking Ahead: Trends & Future Directions
- Offline-First & Edge Resilience Improvements: As edge computing grows, Azure Arc will evolve more offline capabilities, caching of policies/configs, local decisioning.
- Tighter Integration with AI/ML & Data Analytics at Edge: More “data-service-capable” nodes, enabling real time inference/analytics outside Azure, managed via Arc.
- Evolving Governance & Security Controls: More granular controls, richer RBAC, drift detection, automated remediation.
- Custom Extensions & Ecosystem Growth: More community or third-party extensions (for monitoring, configuration, domain-specific workloads) plugging into Arc architecture.
Conclusion
Azure Arc’s architecture, comprised of agents, resource bridge, custom locations, Arc-enabled servers/Kubernetes/data services, ARM, and governance tools, provides a unified control plane over fragmented environments. Its core capabilities unified management, policy and security consistency, data services deployment, lifecycle and configuration management, monitoring, edge support enable organizations to simplify operations, reduce drift, maintain compliance, and accelerate innovation.
FAQ'S
1. What makes Azure Arc different from traditional hybrid management tools?
Azure Arc centralizes visibility and control by extending Azure services directly to non-Azure environments, unlike traditional tools that manage resources separately without unified governance or consistent policy application.
2. How does Azure Arc improve developer productivity?
Developers can deploy applications consistently across clouds and on-premises using GitOps, Kubernetes integration, and centralized DevOps pipelines, ensuring faster delivery, reduced manual configuration, and simplified hybrid deployment lifecycles.
3. Can Azure Arc help with regulatory compliance?
Yes, Azure Arc applies Azure Policy and Defender for Cloud across diverse environments, helping enterprises enforce compliance rules, monitor continuously, and generate centralized audit-ready reports across all connected resources.
4. Does Azure Arc support modernization of legacy applications?
By connecting older servers or VMs into Azure, Arc enables monitoring, security, and automation capabilities, bridging legacy workloads with modern cloud-native operations without requiring full re-architecture or migration.
5. What industries benefit most from Azure Arc?
Industries like retail, healthcare, manufacturing, and finance use Azure Arc to manage distributed environments, standardize operations across hybrid systems, secure workloads, and streamline compliance in regulated, multi-cloud or edge setups.

