Cloud Agnostic Compliance-as-code
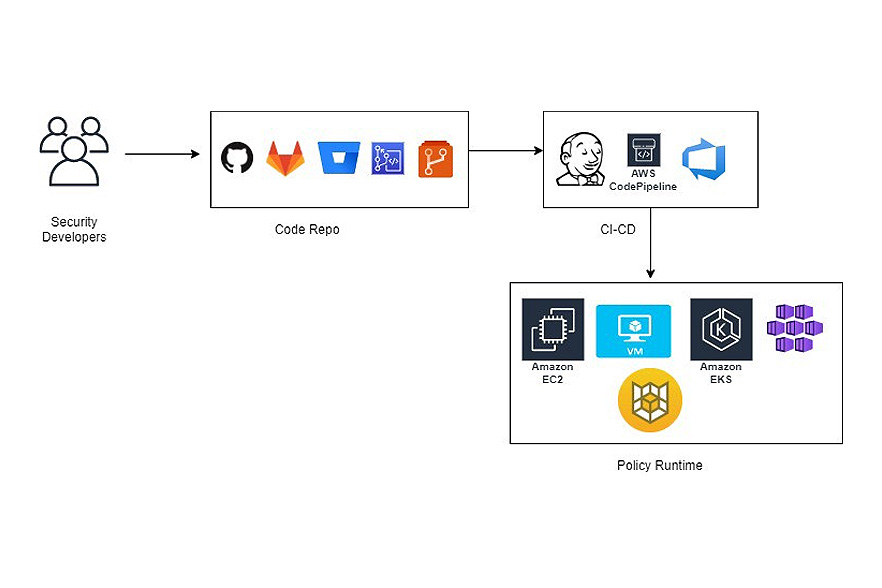
Manage public cloud accounts and resources compliance by defining policies as code for a well managed cloud infrastructure.
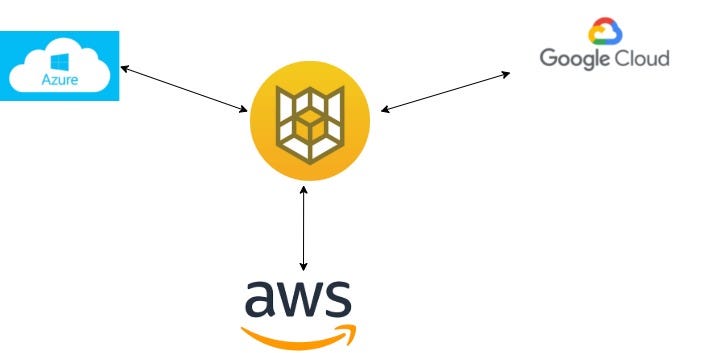
Cloud Custodian
is a rules engine for managing public cloud accounts and resources. It allows users to define policies to enable a well managed cloud infrastructure, that’s both secure and cost optimized.
Custodian policies are written in simple YAML configuration files that enable users to specify policies on a resource type (EC2, ASG, Redshift) and are constructed from a vocabulary of filters and actions.
Benefits:
- Comprehensive support for public cloud services and resources with a rich library of actions and filters to build policies with.
- Supports arbitrary filtering on resources with nested boolean conditions.
- Dry run any policy to see what it would do.
- Automatically provisions serverless functions and event sources (AWS CloudWatch Events, AWS Config Rules, etc)
- Cloud provider native metrics outputs on resources that matched a policy
- Structured outputs into cloud native object storage of which resources matched a policy.
- Intelligent cache usage to minimize api calls.
Three parts:
Cloud Custodian policies contains 3 parts:
- Type of resource to run the policy against (eg: EC2)
- Filters to narrow down the resources (eg: missing a tag)
- Actions to perform on those filtered resources (eg: stop)
Examples:
Enable AWS VPC flow logs if disabled
policies:
- name: vpc-flow-log-check
resource: vpc
filters:
- not:
- type: flow-logs
enabled: true
set-op: or
op: equal
traffic-type: all
log-group: infoservices-VPCFlowLogs
status: active
actions:
- type: notify
template: default.html
priority_header: 1
subject: "VPC Flow Log(s) Not Setup Properly"
violation_desc: "The Following Flow Logs Are Invalid:"
action_desc: "Actions Taken: Notification Only"
to:
- blah-support@infoservices.com
transport:
type: sqs
queue: https://sqs.us-east-1.amazonaws.com/99999999999/info-services-mailer
region: us-east-1Delete unencrypted AWS EBS volume:
policies:
- name: delete-unencrypted-ebs
description: |
Delete all unencrypted EBS volumes upon creation
resource: ebs
mode:
type: cloudtrail
events:
- CreateVolume
filters:
- Encrypted: false
actions:
- deleteDelete Unmanaged Azure disk:
policies:
- name: unmanaged-disk
resource: azure.disk
filters:
- type: value
key: managedBy
value: null
actions:
- type: deleteSample Commands:
# Validate policy for any errors
custodian validate policy.yml
# Perform dry run without impacting the resources
custodian run --dryrun -s . custodian.yml
# Run policy against multiple regions
custodian run -s out --region us-east-1 --region us-west-1 policy.yml
# Run policy against all applicable regions
custodian run -s out --region all policy.yml
# Enable C7n metrics on AWS
$ custodian run -s output -m aws policy.yml
# Enable C7n metrics on Azure
$ custodian run -s output -m azure policy.yml
# Enable C7n logs to AWS CloudWatch Logs
$ custodian run -s output -l policy.yml
# Enable C7n logs to Azure App Insights Logs
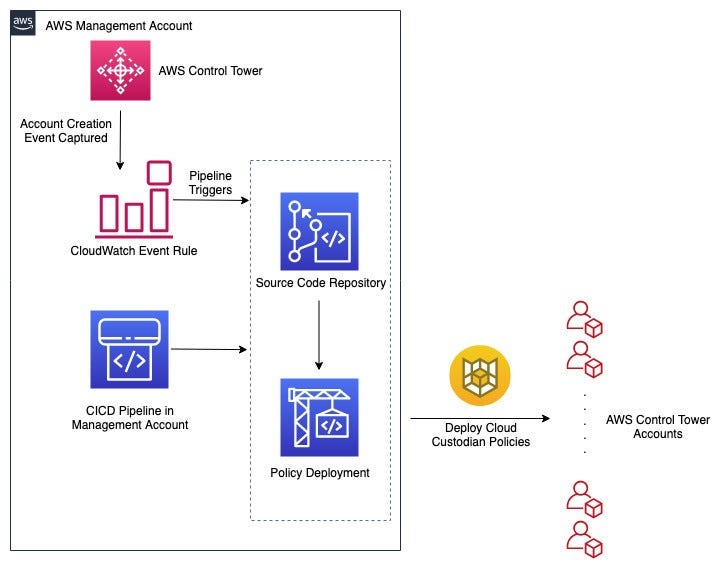
$ custodian run -s output -l policy.ymlDeployment Options:

What Next?
In the next blog installment, we will cover Alert-as-code to see how Python can be used to create alerts on any logs and send notifications to Slack, PagerDuty and others.
Author: Raghavan Madabusi

