Snowflake Platform Access Tokens: Enabling Secure App Integration
Enable secure, scalable authentication with Snowflake's Programmatic Access Tokens (PATs).

Introduction
Snowflake's Programmatic Access Tokens (PATs) represent a significant advancement in how organizations authenticate and secure access to their Snowflake data warehouse. As enterprises increasingly rely on programmatic interactions with Snowflake, traditional authentication methods often create bottlenecks in development workflows and security protocols. PATs solve these challenges by providing a more flexible, secure, and developer-friendly authentication mechanism.
What Are Snowflake Programmatic Access Tokens?
Programmatic Access Tokens are secure, revocable authentication credentials that allow applications, scripts, and services to interact with Snowflake without user password authentication. Unlike traditional authentication methods, PATs are specifically designed for automated processes and service-to-service communications.
These tokens follow the OAuth 2.0 standard, providing a modern approach to securing your Snowflake data while enabling streamlined access for authorized applications and services.
Key Benefits of Using Snowflake PATs
Enhanced Security Through Granular Control
PATs significantly improve your Snowflake security posture by implementing the principle of least privilege. Each token can be assigned specific roles and scopes, limiting access to only what's necessary for each application or service. This granularity reduces the risk surface area by ensuring compromised credentials have limited access to your data environment.
Simplified DevOps Integration
For DevOps teams, PATs eliminate the complexities associated with managing service account passwords and key rotations. Applications can be deployed with tokens that have precisely defined lifespans and permissions, streamlining CI/CD pipelines while maintaining robust security standards.
Improved Audit and Compliance Capabilities
Every PAT carries its own identity within Snowflake's ecosystem, making audit trails more comprehensive and meaningful. Security teams can easily track which token accessed what data, when, and how – essential capabilities for organizations dealing with sensitive data or regulated industries.
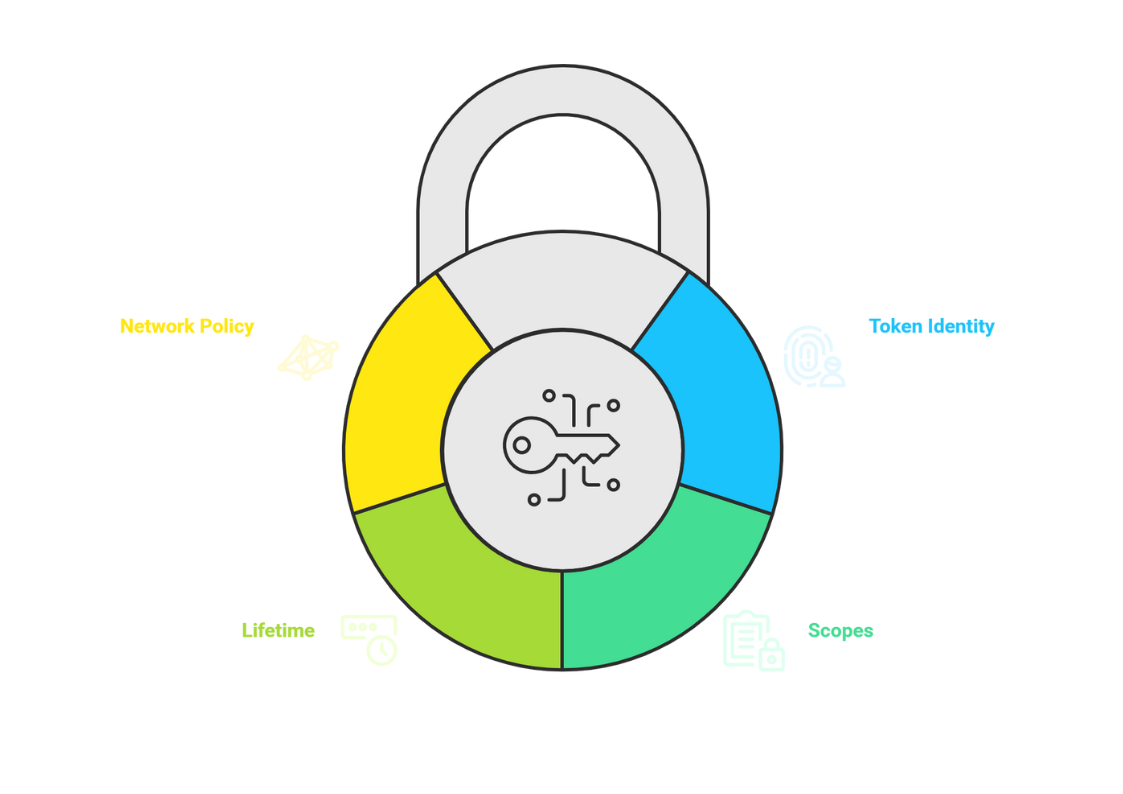
How Snowflake PATs Work
Snowflake PATs operate on a claim-based architecture that defines:
Token Identity: Each PAT is associated with a specific Snowflake user account
Scopes: Defines what operations the token can perform (query execution, metadata access, etc.)
Lifetime: Configurable expiration periods from minutes to months
Network Policy: Optional restrictions on which networks can use the token
When an application or service needs to access Snowflake, it presents the PAT instead of traditional credentials. Snowflake validates the token's authenticity, checks its permissions against the requested operation, and grants or denies access accordingly.
Refer: Official Snowflake Documentation
Setting Up Your First Snowflake PAT
Creating a Programmatic Access Token in Snowflake requires proper permissions and follows a straightforward process:
-- Create a PAT that expires in 60 days
CREATE SECURITY INTEGRATION my_application_pat
TYPE = OAUTH
ENABLED = TRUE
OAUTH_CLIENT = CUSTOM
OAUTH_CLIENT_TYPE = CONFIDENTIAL
OAUTH_REDIRECT_URI = 'https://myapplication.example.com/callback'
OAUTH_ISSUE_REFRESH_TOKENS = TRUE
OAUTH_REFRESH_TOKEN_VALIDITY = 7776000; -- 90 days in seconds-- Generate the actual token
CALL SYSTEM$GENERATE_OAUTH_TOKEN(
'my_application_pat',
'https://myapplication.example.com',
'openid,refresh_token,role:analyst'
);
This example creates a token with specific permissions for an application that needs analyst-level access. The token will expire in 60 days, after which it must be refreshed or regenerated.
Best Practices for PAT Management
Implement Proper Token Lifecycle Management
Establish clear processes for token creation, monitoring, rotation, and revocation. Automated rotation helps ensure that compromised tokens have limited utility, while proper revocation procedures close potential security gaps when access is no longer needed.
Use Scoped Tokens for Different Services
Rather than creating all-purpose tokens, design service-specific PATs with minimal necessary permissions. For example, BI tools might need read-only access to specific schemas, while data pipelines require different access patterns.
Monitor Token Usage with Snowflake's Event Tables
Take advantage of Snowflake’s powerful logging features to monitor how and when tokens are being used.
sql SELECT *
FROM TABLE(INFORMATION_SCHEMA.QUERY_HISTORY())
WHERE AUTHENTICATION_METHOD = 'OAUTH'
ORDER BY START_TIME DESC;
Consistent monitoring can reveal suspicious activity or unusual patterns that may signal token misuse or a potential security breach.
PATs in Snowflake have a few limitations: they can only be active for up to 365 days, and once created, their value can’t be retrieved again. Users can have a maximum of 15 active PATs, and if a token expires or is revoked, it can't be recovered. Learn More
Common Implementation Scenarios
Data Pipeline Integration
PATs are a perfect fit for ETL/ELT workflows, where data pipelines require consistent and secure access to Snowflake without relying on manual credentials. By creating pipeline-specific tokens with appropriate permissions, organizations can ensure data flows securely without embedding sensitive credentials in configuration files.
Microservices Architecture
In distributed systems with multiple microservices accessing Snowflake, PATs provide isolation between services. Each microservice receives its token with tailored permissions, preventing one compromised service from affecting others.
Embedded Analytics Applications
Customer-facing analytics applications can use PATs to create secure, isolated connections to Snowflake. This strategy is especially important for multi-tenant applications, where ensuring strict separation of each tenant’s data is essential.
Troubleshooting Common PAT Issues
Token Expiration Problems
If applications suddenly lose access, token expiration is often the culprit. Implement token refresh mechanisms and alerts for upcoming expirations to prevent disruption.
Permission Configuration Errors
When tokens have insufficient permissions, carefully review the role assignments and scopes. Remember that PATs inherit permissions from their associated role, so the role itself must have appropriate access.
Network Policy Restrictions
If valid tokens are being rejected, check whether network policies are limiting access. Snowflake automatically logs any network policy violations as they occur, providing clear visibility into access issues.
PAT vs PASSWORDS
| PAT | Password |
|---|---|
| Designed for both human and service accounts with a focus on secure, programmatic access. | Primarily intended for human users; often reused or less protected in automated workflows. |
| Has a mandatory expiration, reducing the risk of indefinite access. | May not expire unless enforced by specific account policies. |
| Can be restricted by network policies, allowing access only from approved IPs or locations. | Lacks native network location enforcement, making it more vulnerable to misuse. |
| Can be scoped to specific roles, ensuring minimal privilege access. | Tied to the user’s default role; less granular in access control. |
| Ideal for automation, APIs, and service integrations. | Not designed for programmatic use; prone to being hardcoded or mishandled. |

Conclusion: Embracing Modern Authentication for Data Access
Snowflake's Programmatic Access Tokens represent a significant step forward in balancing security and accessibility for data platforms. By implementing PATs in your Snowflake environment, you gain finer-grained control over access patterns while simplifying authentication for legitimate applications and services.
As data ecosystems grow increasingly complex, authentication mechanisms that combine security, flexibility, and ease of management become essential. PATs provide these capabilities while integrating seamlessly with modern development and operational practices.
For organizations serious about securing their data while enabling programmatic access, Snowflake PATs are no longer optional – they're a fundamental building block of a mature data security strategy.
FAQs
1. How are Snowflake PATs different from traditional password-based authentication?
Answer: PATs are designed for automation in CI/CD pipelines, APIs, and microservices. They differ from passwords in key ways: PATs are time-bound, follow OAuth 2.0, and can be restricted by roles, actions, or IP/network policies. Unlike passwords, which are reusable and pose security risks, PATs offer a more secure and flexible solution for programmatic access.
2. Can I retrieve a PAT value after it’s been created?
Answer: Once a PAT is created, its value is shown only once. If you lose it, you'll need to generate a new token. This helps enhance security by preventing accidental or malicious reuse.
3. What is the maximum number of PATs a user can have active in Snowflake?
Answer: A Snowflake user can have a maximum of 15 active PATs at once. Actively manage and revoke unused tokens to stay within this limit.
4. How do I monitor and audit usage of PATs in Snowflake?
Answer: You can use Snowflake’s INFORMATION_SCHEMA.QUERY_HISTORY() and event logs to track PAT usage. Filtering by AUTHENTICATION_METHOD = 'OAUTH' helps identify which tokens were used, by whom, and when—critical for compliance and security audits.
5. What happens when a PAT expires or is revoked?
Answer: When a PAT expires or gets revoked, it’s done for good—it can’t be reused or refreshed. Any app or service relying on it will immediately lose access. To keep things running smoothly, it’s a good idea to set up alerts and automate token refreshes so you’re never caught off guard or dealing with unexpected downtime.




